Why Does LayerZero Not Truly Satisfy The Bitcoin Consensus
Adam Back, the Bitcoin core development team leader, BlockStream CEO, has a saying: “Great design looks very simple, but the process of designing it is actually extremely complicated.” However, not all product designs that look simple can be called great, such as LayerZero.
Before the cross-chain protocol has an accident, everyone feels that it is very safe and there is no problem, but once an accident occurs, it is a horror event. From the perspective of the number of losses caused by security incidents that occurred on each chain in the past two years, the losses caused by security incidents on cross-chain protocols topped the list.
The importance and urgency of solving cross-chain protocol security issues even exceed the Ethereum expansion plan. Interoperability between cross-chain protocols is an inherent requirement for Web3 to form a network.
Such agreements often raise a huge amount of money, and the TVL and number of transactions are also increasingly driven by rigid demand. However, due to the low degree of public recognition, it is impossible to recognize the security level of these cross-chain protocols.
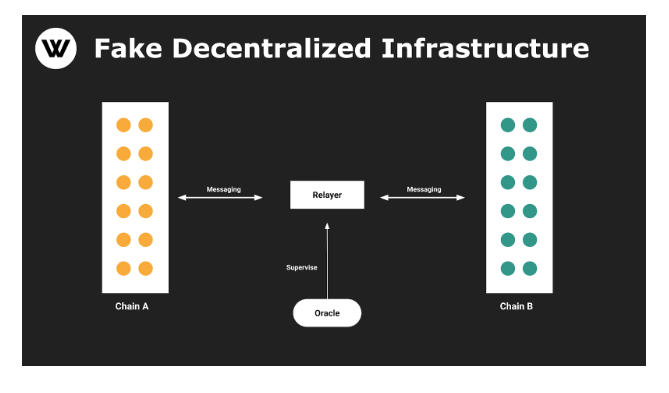
Let’s first look at a product design architecture. The communication process between Chain A and Chain B is performed by Relayer, and Oracle supervises Relayer.
First of all, one advantage of this architecture is that it eliminates the traditional communication between Chain A and Chain B, and the third chain (dApps are generally not deployed on this chain) completes the consensus algorithm and dozens of node verifications, so it can bring end users “Quick cross-chain” user experience.
Because of the lightweight architecture and small amount of code, Oracle has a ready-made Chainlink, so this type of project is easy to go online, but it is also easy to be imitated. The technical threshold can be said to be zero.
There are at least two problems with the above architecture:
- LayerZero reduces dozens of node verifications to a single Oracle verification, and the safety factor is naturally greatly reduced.
- After simplifying to a single verification, it must be assumed that the Relayer and Oracle are independent, and this trust assumption cannot be established forever, which is not enough for Crypto Native and cannot fundamentally guarantee that the two cannot conspire to do evil.
This is the basic pattern employed by LayerZero. As an “ultra-light” cross-chain solution of an independent security type, it is only responsible for forwarding messages and is not responsible for the security of applications, nor has the ability to be responsible.
Then if the Relayer is released and everyone can run the relay, will the above problems be solved? Figure 2 increases the number of Figure 1. First of all, Decentralized does not mean that the number of operators increases and anyone can access it. That is called Permissionless. The demand side has always been permissionless, and making the supply side also Permissionless is not an epoch-making change.
It is a change on the market side and has nothing to do with the security of the product itself. LayerZero’s Relayer is just an intermediary responsible for forwarding information, and its essence is the same as Oracle, which is a Trusted Third Party. Trying to improve cross-chain security by increasing the number of trusted subjects from 1 to 30 is futile. Not only does it not change the characteristics of the product, but new problems will also arise.
If a cross-chain token project allows modification of the configured LayerZero node, it is possible for an attacker to replace it with its own “LayerZero” node, thereby forging arbitrary messages. As a result, there are still huge security problems in projects using Layerzero, and this problem will be more serious in more complex scenarios. As long as one link in the huge system is replaced, it may cause a chain reaction.
LayerZero itself does not have the possibility to solve this problem. If there is a security incident, LayerZero will naturally shift the responsibility to external applications. Because end users need to carefully judge the security of each project using LayerZero, those “user-oriented” projects will carefully access LayerZero to avoid being polluted by malicious applications belonging to the same ecology, so the difficulty of ecological construction is not small.
If Layer-0 cannot share security like Layer-1 and Layer-2, then Layer-0 cannot be called Infrastructure, because the reason why the infrastructure is “basic” is that it can share security. If a project party claims to be Infrastructure, it should provide consistent security for all its ecological projects like other infrastructures, that is, all ecological projects share the security of the infrastructure. So, to be precise, LayerZero is not infrastructure, but middleware. Application developers accessing this Middleware SDK/API are indeed free to define their security policies.
The L2BEAT team once published an article, “Circumventing Layer Zero: Why Isolated Security is No Security?” on January 5, 2023, pointing out that their assumption that the app owner (or someone with the private key) cannot do evil is incorrect. The bad guy, Bob, gained access to the LayerZero configuration.
He can change the oracle and repeater from the default components to components controlled by him and persuade the smart contract using the LayerZero mechanism on Ethereum to let him withdraw all the tokens of the good guy Alice on Ethereum.
The Nomad team issued a document on January 31, 2023, pointing out that there are two key vulnerabilities in the LayerZero repeater, which is currently in a two-party multi-signature state, so these vulnerabilities can only be exploited by insiders or known team members.
The first of these vulnerabilities allowed fraudulent messages to be sent from LayerZero multisigs, and the second allowed the modification of messages or transactions after they were signed by oracles and multisigs, both resulting in the theft of all user funds.
On October 31, 2008, the Bitcoin white paper came out. On January 3, 2009, the BTC genesis block was born. A summary of the white paper A Peer-to-Peer Electronic Cash System is as follows:
“Abstract. A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending.
We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power.
As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they’ll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.”
From this paper, which is of great importance to future generations, people extracted the widely recognized “Satoshi Nakamoto Consensus,” especially from this abstract. Its core feature is to prevent the appearance of a Trusted Third Party and realize trustless Decentralized. The “center” here is A Trusted Third Party. The cross-chain communication protocol is essentially the same as Bitcoin. It is a Peer-to-Peer system. One party sends directly from Chain A to the other party in Chain B without going through any trusted party.
The “Satoshi Nakamoto Consensus” with Decentralized and Trustless features has become the common goal pursued by all subsequent infrastructure developers. It can be said that a cross-chain protocol that does not meet the “Satoshi Nakamoto Consensus” is a fake decentralized cross-chain protocol, and advanced words such as Decentralized and Trustless cannot be used to describe its product characteristics.
And LayerZero introduced itself as Omnichain communication, interoperability, decentralized infrastructure. LayerZero is an omnichain interoperability protocol designed for lightweight messages passing across chains. LayerZero provides authentic and guaranteed message delivery with configurable trustlessness.
In fact, LayerZero not only requires that the two roles of Relayer and Oracle will not conspire to do evil but also requires users to trust the developers who use LayerZero to build applications as a reliable third party and the trusted subjects participating in the “multi-signature” are all Pre-arranged privileged role.
At the same time, it did not generate any fraud proofs or validity proofs during the entire cross-chain process, let alone put these proofs on the chain and perform on-chain verification. Therefore, LayerZero does not satisfy the “Satoshi Nakamoto Consensus” at all, and it is not Decentralized and Trustless at all.
After the L2BEAT team and the Nomad team published well-intentioned articles from the perspective of problem finders, LayerZero responded with “deny” and “deny.” There were many electronic currencies before Bitcoin, but they all failed. Because none of them can achieve the goal of decentralization, anti-attack and inherent value, and the same is true for cross-chain protocols. The probability is that it will end due to insufficient resilience against attacks.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.
Join us to keep track of news: https://linktr.ee/coincu
Website: coincu.com
Harold
Coincu News