What is Malware? Malware distribution attack in crypto 2022
What is Malware? Malware distribution attack in crypto 2022
The form of attack through strange links or fake software is no longer strange to internet users. With the advent of crypto, malware continues to be developed to steal user information as well as use victim’s devices to mine cryptocurrencies.

What is Malware?
Malware distribution attacks are common forms of cyberattacks carried out through malicious software. By creating and using this software, cyber attackers gain access to the victim’s credentials and privileged accounts, thereby performing unauthorized actions on the system and stealing information. personal or business finances.
Some commonly used malware are spyware (spyware), ransomware (ransomware), viruses, and worms (malicious software that can spread)… into the victim’s system through a fake link or software.
What is a Malware Distributing Attack in Crypto?
Crypto Malware is malicious software that is installed on a victim’s computer after they click on a phishing link or download a compromised software. Malware distribution attacks can be used for many different purposes such as mining cryptocurrencies by using the victim’s computer resources, accessing personal information such as private keys, stealing Bitcoins, electricity death, and fiat… without the victim knowing.
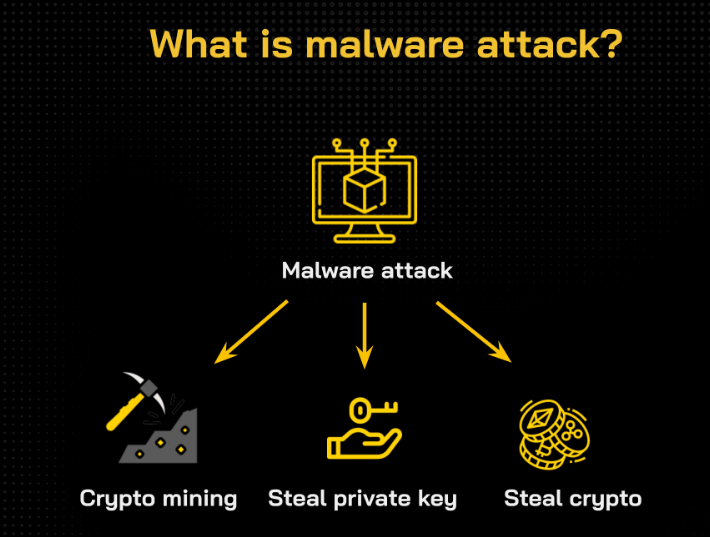
Types of malware attacks in crypto
Cryptocurrency Mining Through Malware
To understand how malware mines cryptocurrencies, it is first necessary to understand what crypto mining is.
Crypto mining, or “mining”, is the process of creating a coin, in which “miners” solve complex mathematical equations to confirm transactions on the blockchain, thereby generating new blocks. This activity is legal and miners will be rewarded with cryptocurrencies.
Mining cryptocurrency through malware is also known as crypto-mining malware or cryptojacking. When clicking on an unfamiliar link or downloading a compromised software, the infected victim’s computer automatically launches the malware, mines cryptocurrency, and sends it back to the attacker’s wallet.
In most cases, this crypto-malware can run independently indefinitely after executing on the victim’s device. Whenever the victim uses his device, malware is launched. The victim will not receive any crypto assets while suffering severe loss of computing resources and processing power. This way the attackers can get a steady profit – as long as it goes undetected.
Another “advanced” method of infection is through compromised advertising or websites. When a user visits an infected website, the script will automatically run on their device. This form of attack is even more difficult to detect because the malicious code is not stored on the computer but in the browser.
Since 2019, a piece of malware masquerading as the Google Translate app has surreptitiously infected some 112,000 computers across 11 countries, forcing them to mine Monero (XMR) and send it to the attacker’s wallet. personnel of these devices does not know.
Steal Private Keys, Bitcoins, and Cryptocurrencies
Malware that collects and retrieves data from users’ hot wallets or non-custodial wallets is called “Cryware”. This software focus on attacking wallets that act as browser extensions (e.g. MetaMask, Coinbase Wallet, etc.), which allow attackers to access wallet data and quickly transfer crypto assets to your wallet. And because they are blockchain transactions, this theft is irreversible.
Most Cryware is capable of attacking hot wallets from the Chrome browser. Firefox and Opera browsers don’t appear to be vulnerable to extensions-specific cyberattacks, but they can still be targets for site credential attacks.
Cryware also targets files that store private keys, stealing information and removing all traces of theft. One of the most popular Cryware is Mars Stealer, with the ability to attack more than 40 browser crypto wallets to steal private keys. Mars Stealer can even be purchased on the dark web for as little as $140, making it easy for bad guys to access this rogue tool.
Another popular Cryware is Clipper, which has been active since 2017. Clipper uses the user’s clipboard to replace the target crypto address with the hacker’s. When victims copy and paste a wallet address to pay a friend, they are transferring money to the attacker. Since crypto addresses are often very long, they can be easily overlooked by victims, even when trying to compare each address character. Clipper encryption software has been found on the foundation of Bitcoin and Ethereum.
Steps to take to avoid malware attack
There are a few things users can do to reduce the risk of crypto-malware attacks:
- Lock hot wallets when not trading often. Disconnect websites connected to hot wallets.
- Do not store private key information in plain text (which can easily be stolen) and be careful when copying and pasting password information.
- Close the browser session each time the transaction is complete.
- Watch out for suspicious links to wallet websites and apps, and double-check crypto wallet transactions and approvals.
- Do not share private key information or seed phrases.
- Use wallets with multifactor authentication or hardware wallets to store private keys offline.
- Double-check all file extensions you download.
Verdict
Accessing unknown links or downloading compromised software creates huge risks for crypto users. With sophisticated attack methods, using users’ computers to mine crypto or steal private keys and other cryptocurrencies, malware attack threatens the majority of crypto users.
DISCLAIMER: The Information on this website is provided as general market commentary and does not constitute investment advice. We encourage you to do your own research before investing.
Join CoinCu Telegram to keep track of news: https://t.me/coincunews
Follow CoinCu Youtube Channel | Follow CoinCu Facebook page
Lucian
CoinCu News













